CMMS and Cybersecurity: Strengthening Your Defense in Industry
The Case for Security
Would you be comfortable knowing that complete strangers were wandering around your yard and inside your house? Most of us would say, “No way!”, even if we trust that most people don’t have malicious intent. We have locks on our doors and fences as a guard against the few bad people we know are out there.
Security is essential in both the physical and digital worlds. The industrial internet of things (IoT) devices, programmable logic controllers (PLC), and distributed supervisory control and data acquisition (SCADA) systems that comprise Industry 4.0 bring a wide variety of benefits. These operational technologies (OT) increase productivity and quality control, but they also expand potential digital vulnerabilities.
Operational Technology (OT) and Information Technology (IT) have similar potential risks but are not always on the same page in terms of security control capabilities. I’ve been installing anti-malware and anti-virus protection on my computer for decades. Are we doing the same thing on our manufacturing operational IoT-type networks? We have seen plenty of headline-grabbing computer hacks over the past few years from a variety of nefarious actors. Small or large, operations teams need to take cybersecurity seriously.
Cybersecurity Needs on the Rise
Cybersecurity is the protection of networks, computers, and intellectual property from theft or damage. Its goal is to avoid unauthorized information disclosure and disruption to the integrity or availability of services.
Unfortunately, cybersecurity risks exist in places often overlooked by operations leaders. The untold numbers of devices in our world and their expanding interconnectivity increase risks exponentially. What is potentially at risk? Any device is connected to the internet, your local network, Wi-Fi, or Bluetooth! In addition, any supplier you are connected to digitally is a risk.
The impact of cybersecurity incidents on your organization can be expensive and disruptive, and the number of incidents is on the rise. According to an NTT Global Threat Intelligence report from May 2021, the manufacturing sector experienced a 300% increase in worldwide cyber-attacks since the start of the COVID pandemic. These attacks include well-publicized incidents such as the Colonial Pipeline and JBS but also hundreds of others impacting companies large and small.
Developing an OT Cybersecurity Program
The first steps in mitigating potential cyber threats are understanding the risks most applicable to your operation. The cybersecurity risks faced in manufacturing include:
- Phishing attacks
- Ransomware
- Equipment compromise
- Intellectual Property Theft
- Insider Threats
- Supply Chain Attacks
- Nation State Attacks
The most effective means to prioritize and start remediation on these risks is to adopt a formal OT cybersecurity program with a dedicated champion. In most organizations, OT cybersecurity will fall under the scope of IT cybersecurity. For this program to be successful, OT and IT must be in sync. This synchronization can be challenging because some standard IT security practices do not translate directly within the OT world. For example, a routine IT activity such as patching vulnerable software can be problematic in OT if it results in equipment downtime.
Some common cybersecurity considerations are broadly applicable to a variety of use cases:
- Provide employee training on how to recognize and respond to phishing attempts. Ensure your suppliers provide similar training for their employees.
- Train staff in best practices, including the importance of strong and unique passwords. Reference this password checklist for more information.
- Develop a business continuity plan that includes off-site backups of all business-critical systems. Restrict device and system access to only authorized personnel using a least-privilege approach (only grant as much privilege as needed to complete the authorized task).
- Define company-wide policies for secure remote access. Cover both employees and suppliers under these policies.
- Limit access for tasks such as internet browsing and email within your OT environment. Restrict this type of access to your business networks.
- Create an accurate inventory of all technology assets within your OT environment. Where possible, implement a patch and vulnerability management program for these assets.
- Develop a plan to respond and recover from a cyberattack, including notifying all affected employees to update their passwords immediately. You may need to notify attorneys general in states where you conduct business. Ensure the plan is rock-solid by performing workshops and drills to stress-test your plans.
None of this is easy or convenient, but the consequences of a cyberattack with poor or no prevention can be incredibly damaging. As your culture accepts these new tasks, the process and protection get easier.
Cybersecurity and CMMS Vendors
Computerized maintenance management systems (CMMS), one of many industrial software solutions, are becoming ubiquitous in many industries. The security of your CMMS vendor is an important consideration in your overall supplier security program. Security for your CMMS is a shared responsibility between the software vendor, the CMMS administrator, and the actual end-users.
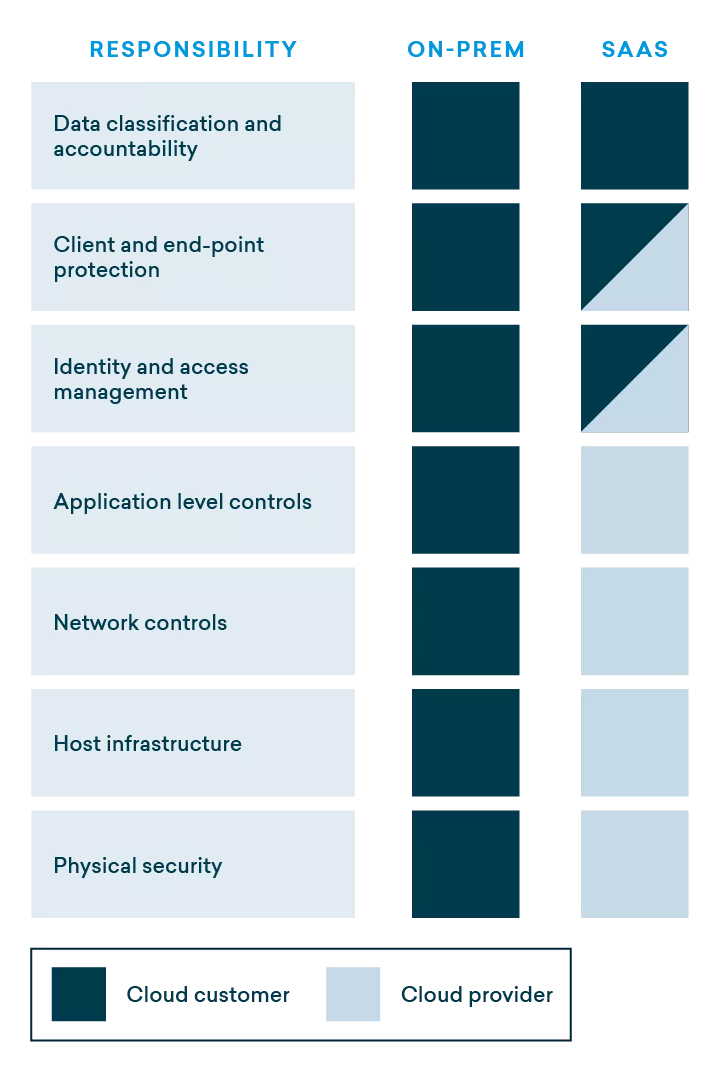
The “shared responsibility” model of cybersecurity is widely used within IT. Before adopting this model to consider appropriate CMMS cybersecurity controls there is an important distinction to be made. Is your CMMS on-premises (installed on your organization’s servers) or cloud-based (also call Software as a Service or SaaS)? As you will see, not only is SaaS/cloud-based superior for many reasons, but you can also add security to this list.
In a SaaS implementation, many of the security controls fall to the vendor. Using a SaaS vendor provides your organization with many advantages such as mitigation of risk, cost savings, scalability, and resilience. However, it is critically important that you thoroughly vet your vendor’s security program.
You should insist that your SaaS vendors provide transparency about their security program. Focus your SaaS vendor evaluation on the following areas:
- Your IT team should play an important role in helping you evaluate vendor security.
- Review the SaaS vendor’s patching policies. They should be regular and ongoing at no more than monthly intervals.
- The SaaS vendor’s application should provide features that allow you to integrate with your internal security controls. These integrations include Single Sign-On (SSO) options, Role-based Access Controls (RBAC), and audit logs.
- Know where your data is stored. Include the storage of backup data in this line of questioning.
- Make sure that the SaaS terms of service give you ownership of your data and restrict data sharing by the vendor.
- Ensure the SaaS vendor complies with relevant regulations. In the U.S., this includes the California Consumer Privacy Act (CCPA). If you are international, the General Data Protection Regulation (GDPR) may be important.
- Identify sub-services used by the SaaS vendor. Most SaaS vendors work with a variety of sub-service providers such as Amazon AWS or Microsoft Azure for data center hosting. Ensure these sub-service providers are reputable and that they do not introduce the potential for unexpected data storage locations.
- Review SaaS vendor third-party audits. Third-party audit reports such as penetration testing and risk assessments will help confirm the effectiveness of the vendor’s security controls.
Learn more about our approach to innovative, secure and accessible technology
CMMS Administrator responsibilities are key to avoiding cybersecurity issues. As recommended above, you should make sure that your CMMS supports SSO, RBAC, and audit logs. Make use of all of these!
Work with your IT team to make sure SSO is implemented and use RBAC to enforce appropriate access and permissions for all users. A good CMMS will have excellent control over “who can edit what.” I’ve personally seen situations where unauthorized users edit other staff’s work orders, delete data they should not, and perform other harmful incidents—all because of lax permissions. CMMS Administrators should also regularly review CMMS access and change logs to help identify possible cyber threats.
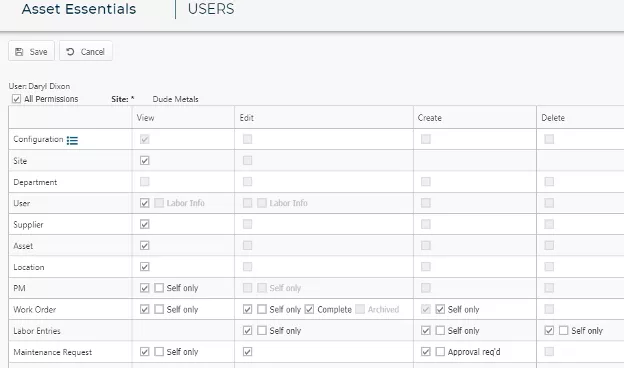
Detailed, role-based control allows administrators to create view, edit, create and delete-based permissions.
Technicians and non-technical maintenance staff may not think it, but they have considerable exposure to potential cyber-attacks. They often need to access both internet-connected business systems and OT systems. They are also major end users of CMMS software. How can we help keep personnel secure?
A robust employee cybersecurity training program that focuses on recognizing and responding to phishing is a great start. Other end user cybersecurity tips:
- Be careful with login credentials. Sharing passwords is always a bad idea. Use long, strong, and unique passwords (hackers will easily crack your pet’s name)
- Be cautious with unvetted USB devices (“thumb drives” or similar)
- Keep your mobile device safe and always use password or facial recognition.
- Use secure, trusted Wi-Fi
- When working from home, use firewall protection and company-approved VPN or other technologies for connecting to work systems
Conclusion
No one is asking to be “hacked,” but we sure make it easy for bad actors to try by keeping our head-in-the-sand mentality when it comes to cybersecurity. Changing passwords easily falls under the “PITA” category, but what is far worse is a cyberattack where you take real damage. Like other good preventive measures, embracing and adhering to cybersecurity best practices takes an investment, but is well worth it.




